Exploiting HTTP Request Smuggling to Deliver Reflected XSS
Cybersec Café #5 - 04/08/2024
Welcome back to Methodology Monday at the Cybersec Cafe - the weekly dive into the mind of a Hacker. Join us every Monday as we dive into diverse lab environments, unraveling the art of recon, testing, and exploitation across various vulnerabilities.
Objective
Employ HTTP Request Smuggling techniques to smuggle a request to the backend server, triggering a victim user to receive a response containing an XSS payload executing alert().
What is HTTP Request Smuggling?
HTTP Request Smuggling is a sophisticated web attack exploiting inconsistencies in how servers interpret HTTP requests. By manipulating server components' parsing techniques, attackers can smuggle malicious payloads into the server's communication flow, leading to serious security risks such as data theft or XSS injections.
What is Cross-Site Scripting (XSS)?
Cross-Site Scripting (XSS) is a common web vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. This occurs when a web application incorporates untrusted data into its output without proper validation or escaping. When users interact with the compromised page, the injected scripts execute within their browsers, enabling attackers to steal sensitive information, hijack sessions, or perform other malicious actions.
Methodology
The Recon
As with every approach to an application, the Methodology begins with the Recon phase.
What we know going into the lab is that our inflection point for the Reflected XSS payload in the User-Agent header.
On top of this, despite the support for HTTP/2 in the lab environment, our intended solution today requires downgrading the request to HTTP/1.1.
Additionally, the lab environment mirrors victim behavior, with each POST request we send, the lab triggers a corresponding victim Request.
Upon initial inspection, the application presents itself as a Simple Blog platform, featuring a Comment functionality within each blog post, allowing all visitors to interact and post comments.
Outside of this comment feature, there is really no obvious functionality or input vectors that stand out.
You can view our full SiteMap here:
To commence our reconnaissance efforts, we can start our automated approach by initiating a scan on the Root Request along with the Comment Functionality.
Notably, the lab advises leveraging the HTTP Request Smuggling Burp Extension to expedite our reconnaisance by testing for the vulnerability using time delays.
You can kick this off by sending a request over to the Repeater, right clicking the request, then navigating to: Extensions > HTTP Request Smuggling > Smuggle Probe
This combined approach streamlines the automated detection of vulnerabilities and creates a Proof-of-Concept payload for executing our Request Smuggling vulnerability.
Testing
Upon the completion of our automation, the HTTP Request Smuggling Extension reveals intriguing findings, flagging a potential CL.TE vulnerability through the detection of response delays. Enclosed are some demo requests:
We can also see that additionally, our Active Scans generated some payloads for us:
From these scans, we have virtually confirmed the presence of a Request Smuggling vulnerability, leaving only manual verification pending.
In order to execute our attack successfully on the victim, we must also determine how to inject a reflected XSS within the application.
As a gentle reminder, we were told that the XSS vulnerability will leverage the User-Agent header within the application's architecture.
Looking through the Site Map, we can identify that the GET request to retrieve a blog post contains the User-Agent header.
We can send this request to our Repeater and see if there is any reflection of this header in the Response:
In order to verify that we can utilize this User-Agent header as an injection point, we can inject an arbitrary value to test if there is reflection:
We can see that this works!
Now we can craft a payload.
By analyzing where the User-Agent header gets reflected in the Response, we can draft up the following payload:
test”/><script>alert(1)</script>
This will escape the payload out of the string value, then inject a script tag directly into the DOM.
Now, let’s put it all together.
Exploitation
We can start by sending one of the POC Request Smuggling requests from our scans over to the Repeater:
Here are some essential points to highlight:
Downgrade the request protocol to HTTP/1.1, which can be configured in the Inspector tab located on the right-hand side.
Ensure to uncheck the "Update Content-Length" option under settings, allowing us to freely manipulate the Content-Length Header.
Verify the Transfer-Encoding: chunked header is present.
Following this, we can eliminate any extraneous components from the requests.
For the initial request, retain only the following headers:
Host
Content-Type
Content-Length
Transfer-Encoding
Subsequently, we can concatenate the second request as a chunked request onto the end of our first, ensuring to retain only the essential headers:
User-Agent
Content-Length
Content-Type
Make sure that both requests have been downgraded to HTTP/1.1
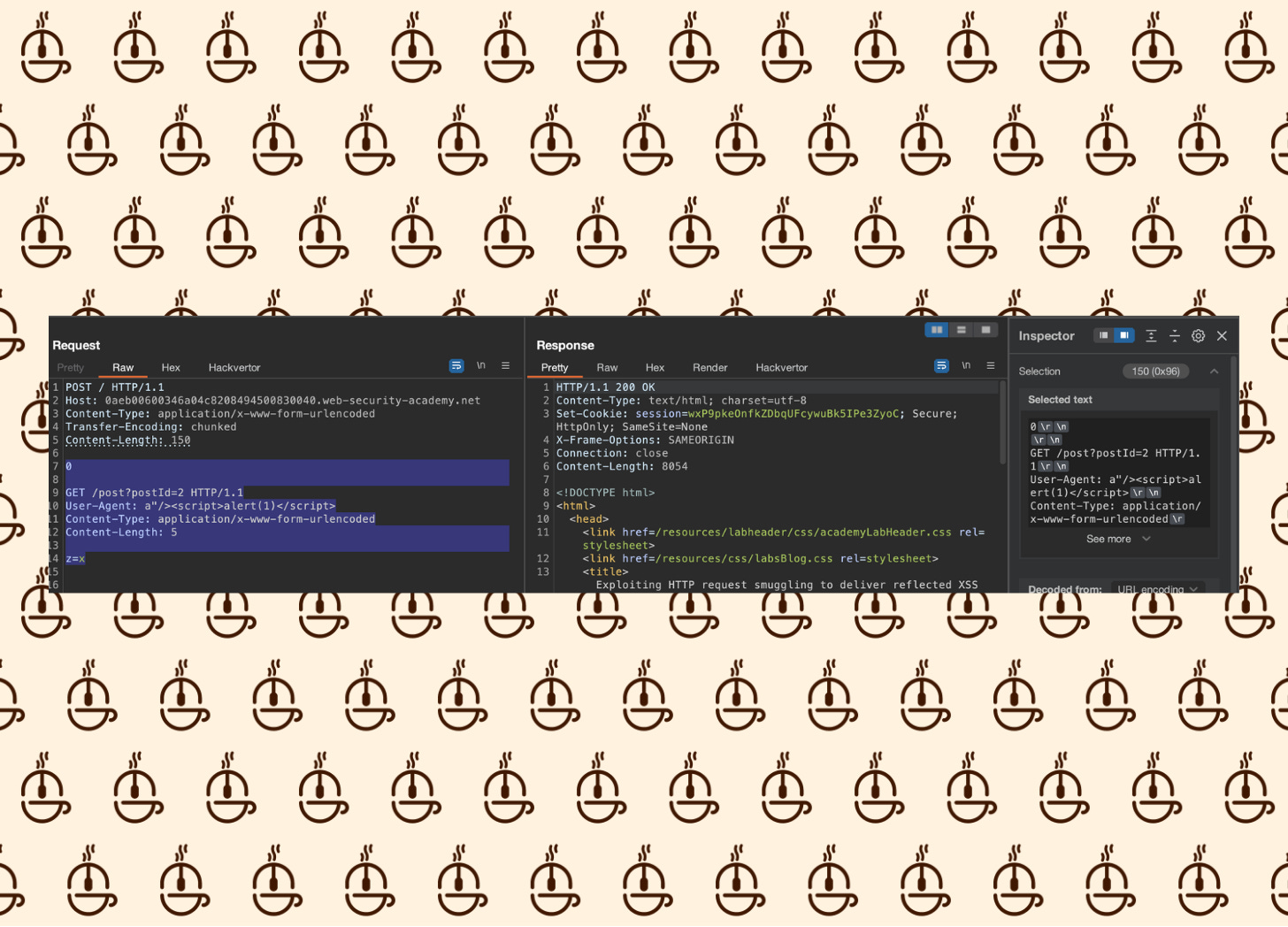
To obtain the Content-Length value for the first request, highlight everything from the end of the headers to the "X" value, then check the length in the Inspector tab located on the right side:
To determine the Content-Length of the second request, select everything beneath the headers of the second request and once more observe the length in the Inspector tab.
Now, let's send this request and witness the successful smuggling of the reflected XSS payload to our victim user!
What We’ve Learned
In this walkthrough, we’ve demonstrated the potential for chaining Request Smuggling and XSS to orchestrate sophisticated attacks against unsuspecting users. Through this method, attackers can exploit systemic weaknesses in web application infrastructures, enabling the delivery of malicious payloads. This underscores the imperative need for robust security measures and proactive vulnerability management to safeguarding users from compromising their data.
Want to give the lab a try yourself? You can check it out on PortSwigger’s website here.
Securely Yours,
The Cybersec Cafe
Just a heads up, The Cybersec Cafe's got a pretty cool weekly cadence.
Every week, expect to dive into the hacker’s mindset in our Methodology Walkthroughs or explore Deep Dive articles on various cybersecurity topics.
. . .
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X or my Website. Can't wait to keep sharing and learning together!