I Wish I Knew This When I Started in Cybersecurity
Cybersec Café #78 - 08/05/25
Whether you’re new to the industry or pivoting into cybersecurity, I’m here to tell you that it’s easier than you think to stand out in this hyper-competitive field.
But, I’m blown away by how many professionals I’ve met who never do it, and also those who have no aspirations to do it.
And no, I’m not going to tell you to chase another certification.
Sure, certs can help if you need a foot in the door. But if you’ve been following this newsletter for a while, you’ll know I’m a big fan of building tangible skills, not just collecting PDFs.
Because the people who make a real impact in cybersecurity? They’re the ones who build, break, and solve things. Not the ones who spend every other month cramming for an exam.
Here’s the secret: get technical from day one.
That’s it.
Now, I get it - you’re probably thinking, “Okay Ryan - Sure, getting technical sounds great in theory, but what does that actually mean in practice?”
In this article, I’ll give you the foundations to get started. And the best part? Everything you absolutely need to learn is free.
But, the rest is up to you.
The Foundation
This is where it all begins. If you’re serious about building technical skills in cybersecurity, you need to start with the core concepts.
They may not be glamorous or exciting, but they’re critical. These fundamentals will form the mental scaffolding for future concepts, tests, and solutions you’ll encounter throughout your career.
Everything you learn will build upon these foundations in some way, so take the time to truly understand them. I’ll give you exactly what you need here to get started, but I challenge you to be curious and dive deeper into them.
Infrastructure Basics
Firewalls
Firewalls are security devices or software that monitor and filter network traffic based on a defined set of rules - either incoming (ingress) or outgoing (egress) traffic. Think of them as digital security guards standing at the perimeter of your device or network.
There are two primary types:
Host Based: Installed on individual machines to filter traffic specific to that device. (Ex. Windows Defender Firewall)
Network Based: Deployed at the edge of a network to control traffic between the internal network and internet. (Ex. Palo Alto, Cisco ASA)
Misconfigured firewalls are one of the easiest ways attackers can sneak in. As a security engineer, you’ll frequently need to review logs or help create firewall rules - especially during security incidents.
Network Basics
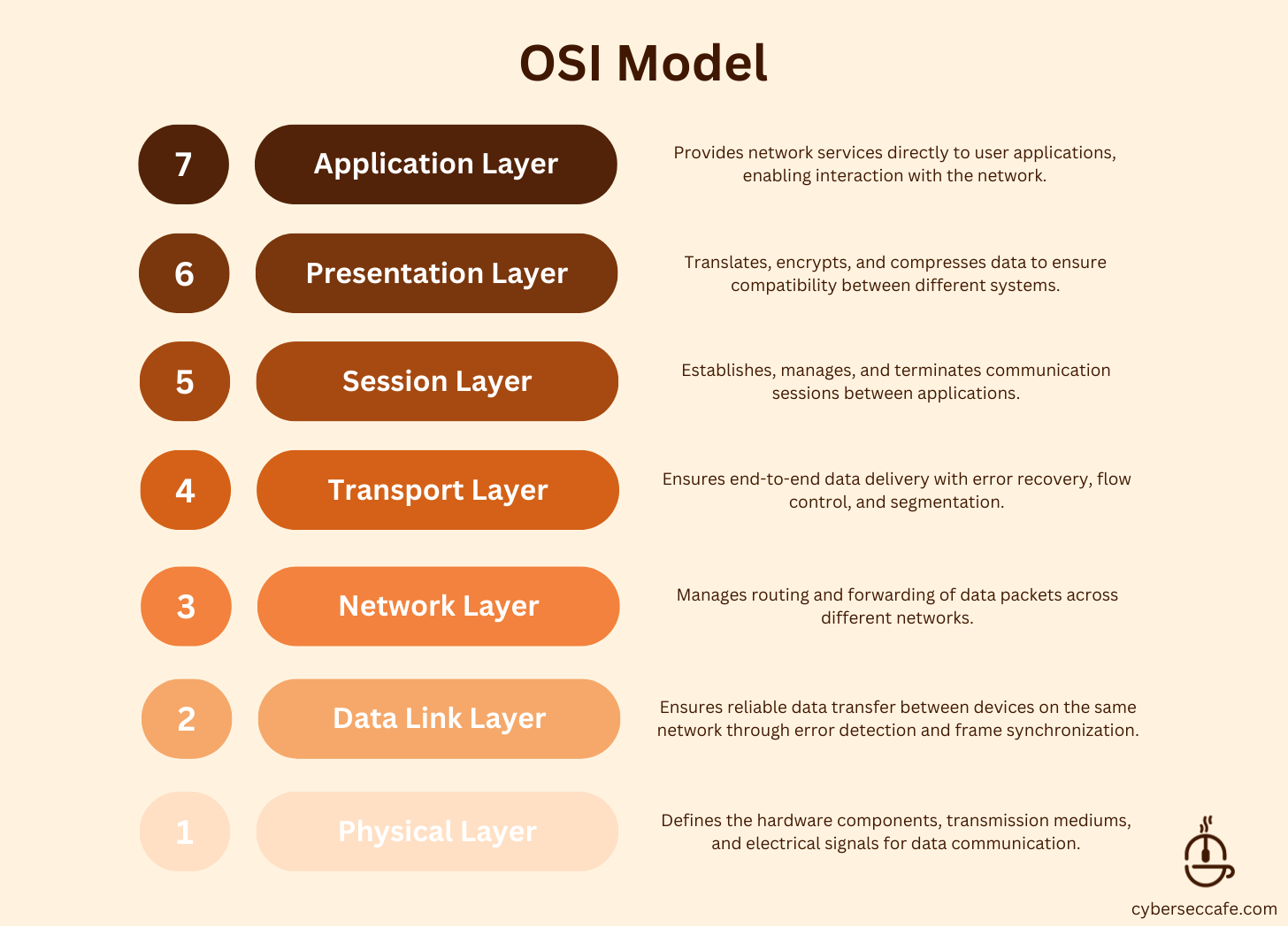
To understand how systems communicate, you need to understand the OSI model. It breaks networking into 7 logical layers:
It consists of 7 layers:
Physical: Hardware like cables and switches.
Data Link: Manages MAC addresses and switching on local networks.
Network: Routes data across networks using IP addresses, subnets, and routers.
Transport: Ensures reliable data delivery.
Session: Manages communication sessions between applications.
Presentation: Handles data formatting, encryption, and compression.
Application: The user-facing layer (e.g. web browsers, email clients).
Each layer relies on specific protocols for communication. Here are some common ones you’ll run into:
TCP (Layer 4): A reliable, connection-oriented protocol used fin most web traffic and email
UDP (Layer 4): A faster, connectionless protocol used for streaming, DNS, and VoIP.
ICMP (Layer 3): Used for diagnostics and often abused by attackers during reconnaissance.
SFTP (Layer 7): Secure file transfer using SSH, differing from the insecure FTP protocol.
Each layer also has ports associated with various services. They’re often tied to Layer 4 protocols:
22 - SSH: Secure shell access to remote machines.
53 - DNS: Domain name resolution.
80 - HTTP: Unencrypted web traffic.
443 - HTTPS: Encrypted web traffic.
Web Protocols
Whether it’s tooling or applications, much of what we deal with as security engineers involves the web in one way or another.
That’s why it’s essential to understand how the web works at a foundational level
As I mentioned earlier, ports 80 and 443 are delegated by default to HTTP and HTTPS. The differences between the two are:
HTTP: Data is sent in plaintext and is vulnerable to sniffing.
HTTPS: Data is encrypted via TLS, protecting it in transit.
Over these protocols, web applications use core HTTP methods to communicate:
GET: Retrieves data.
POST: Submits data.
PUT: Updates or replaces data.
DELETE: Removes data.
There are also three fundamental components to understand how web applications work and how all aid the layered security approach:
Cookies: Store session data on the client side and can be hijacked if not properly secured.
Headers: Metadata passed with requests and responses.
Sessions: Track users after login and are crucial to maintain state and identity.
Getting a handle on these web basics will help you contribute confidently in web security conversations.
DNS
DNS is a foundational topic to how the internet works. It’s essentially the internet’s phone book.
It translates human-readable domains into machine friendly IP addresses.
At a high level, DNS resolution involves a recursive lookup process, typically flowing form:
Local DNS Resolver
Root Name Server
Top-Level Domain (TLD) Name Server
Authoritative Name Server
Each step helps you route to the correct IP address behind a domain.
I highly recommend watching this explanation video from PowerCert on YouTube for all the details:
Cybersecurity Basics
Now that you’ve covered the foundational knowledge of how networks and the web work (from a mile-high view), it’s time to jump into some cybersecurity basics - after all, that is the industry you’re looking to get into.
Authentication vs Authorization
At its core, cybersecurity is about ensuring secure access to data. That starts with secure applications.
Applications rely on two key concepts:
Authentication: Verifies who you are. (Ex. username/password, MFA code, fingerprint scan)
Authorization: Determines what you’re allowed to do after you’ve been authenticated.
These two go hand-in-hand: authentication gets you in the door, and authorization determines what rooms you can access once you’re inside.
Encryption
Encryption is one of the most fundamental cybersecurity concepts - and for good reason.
It’s all about protecting data from unauthorized access by converting it to unreadable formats.
There are two main types:
Symmetric: Uses the same key to encrypt and decrypt data. It’s fast, efficient, and great for large volumes of data. (Ex. AES)
Asymmetric: Uses a public key to encrypt and a private key to decrypt. It solves the key exchange problem and enables use cases like secure web browsing, email encryption, and digital signatures. (Ex. RSA)
A real world example: When you visit a website over HTTPS, asymmetric encryption helps initiate the secure connection. After the handshake, symmetric encryption takes over for faster performance.
Hashing
Hashing is the process of turning data into a fixed-length string using an algorithm. Unlike encryption, it’s one-way - meaning you can hash data, but you can’t “unhash” it.
But here’s the key: the same input will always produce the same output when using the same hashing algorithm.
It’s important to note that hashing is not encryption. It’s not meant for secrecy, it’s meant for integrity. And it’s not secure by default. Hashes can be brute-forced or cracked using rainbow tables if they’re not properly salted.
Some common use cases for hashing algorithms, like SHA256 and MD5, are:
Password Storage: Hash and salt password before saving them to a database.
File Integrity: Verify a file hasn’t been tampered with.
Digital Signatures: Ensure authenticity and data integrity.
Popular Vulnerabilities
Or as I like to call them: the ticket sellers of cybersecurity.
Let’s be real - most of us got interested in this field because of the hacks, the breaches, and the drama we saw in news articles. That’s why you should know about the most common (and some of the coolest) vulnerabilities:
Cross-Site Scripting (XSS): Allows attackers to inject malicious scripts into web pages. It’s often used to steal cookies or hijack sessions, but can be prevented with proper input sanitization and proper output encoding.
SQL Injection (SQLi): Attackers can manipulate SQL queries via user input to access or modify data they shouldn’t. It’s common in poorly coded login forms or search boxes and can easily be mitigated by using parameterized queries.
Buffer Overflow: Happens when more data is written to a buffer than it can handle and can lead to crashing or code execution. It’s typically found in lower-level languages like C and C++.
Command Line
You can’t be effective in security without getting comfortable in the terminal.
Whether you’re on Linux, macOS, or Windows, the core concepts stay the same - you’ll just need to learn the different syntaxes.
Mastering the command line will help you navigate systems, investigate EDR alerts, use command-line tooling - all while looking like a pro hacker in the coffee shop.
Here are a few foundational basic unix based commands to know:
Navigating Files
cd - Used to move between folders
Ex. cd /var/log
ls - View files and directories in the current folder
Ex. ls
cat - Concatenate and view file content in the terminal
Ex. cat config.txt
find - Search for files
Ex. find / -name “*.log”
Permissions
chmod - Change file permissions to control who can read, write, or execute files
Ex. chmod 755 script.sh
chown - Change the owner or group of a file
Ex. chown root:admin secure.txt
unmask - Sets default permissions when new files/folders are created
Ex. unmask 022
sudo - Execute a command as superuser
Ex. sudo npm install package
Network Troubleshooting
ping - Tests is a host is reachable and how fast
Ex. ping cyberseccafe.com
traceroute - Track the path to a host
Ex. traceroute cyberseccafe.com
curl - Send requests to web servers
Ex. curl -I https://www.cyberseccafe.com
nmap - Scan hosts and networks for open ports and services
Ex. nmap -sV 192.168.1.1
If want hands-on practice, a brilliant resource for learning command line fundamentals is OverTheWire’s Bandit challenge: https://overthewire.org/wargames/bandit/
SQL
SQL isn’t just nice to know anymore - it’s a must-have.
In a field driven by logs, alerts, and data streams, your ability to extract insights with a simple query can make or break an investigation.
Even if your tooling doesn’t use SQL directly, most security platforms use SQL-inspired languages (like KQL, Lucene, or SPL).
Start with these core SQL concepts and dig down from there:
SELECT - Choose the columns you want to view
Ex. SELECT username, login_time
FROM - Specify the table where the data lives
Ex. FROM login_events
WHERE - Filter rows based on conditions using operators like:
= (Exact Match)
WHERE status = ‘failed’
LIKE (Pattern Matching)
WHERE email LIKE ‘%@gmail.com’
IN (Multiple values)
WHERE country IN (‘US’, ‘UK’, ‘CA’)
LIMIT - Restrict the number of rows returned.
Ex. LIMIT 50
ORDER BY - Sort the results
Ex. ORDER BY timestamp DESC (most recent events first)
GROUP BY - Aggregate similar values
Ex. GROUP BY ip_address
COUNT() - Count rows returned. Often used with GROUP BY
SELECT ip_address, COUNT(*) FROM logins GROUP BY ip_address
You can use a resource like SQL Practice and SELECTY to write, test, and understand queries in real time.
If you want to go deeper, I’d suggest reading my article Why Knowing How to Query is an Essential Cybersecurity Skill.
Prepare for a career in Cybersecurity, one sip at a time with The Security Sip. With rapidly evolving threats and technologies, many struggle to gain the right skills and experience to break into the cybersecurity industry. This course is designed to transform beginners into industry-ready professionals over 12 sections, 85 modules, and 155 exercises. Check it out!
Programming with Python
With so many languages out there, choosing where to start can often feel overwhelming.
Truthfully, you can pick almost any major programming language and be fine. But if you’re heading into cybersecurity, I strongly recommend starting with Python. Here’s why:
It’s beginner friendly and reads like plain English.
It makes automation easy - perfect for eliminating repetitive tasks.
It helps you focus on problem-solving, not memorizing confusing syntax.
It’s widely used across the security landscape - from detection engineering, to incident response, SOAR, and open-source tooling.
The best part is you don’t even need to master complex topics. If you get the basics from this article, you’re off to a strong start.
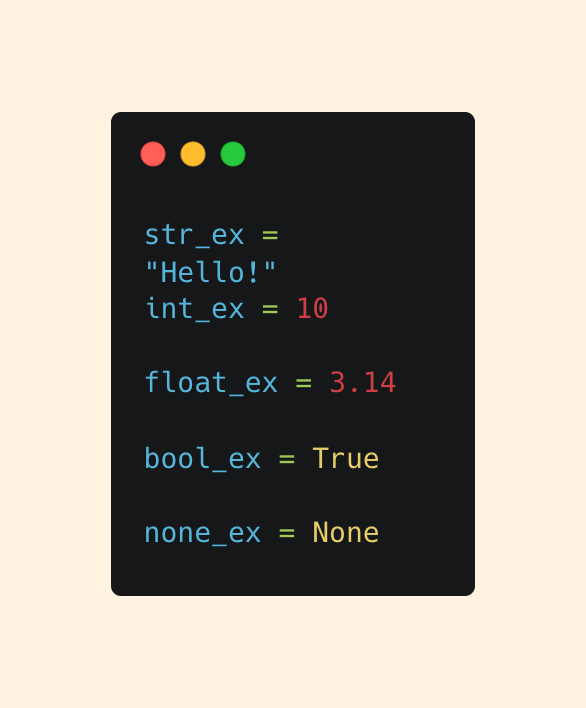
Basic Data Types
Strings (str) - text
Integers (int) - whole numbers
Floats (float) - decimal numbers
Booleans (bool) - True or False
NoneType (None) - Represents the absence of a value
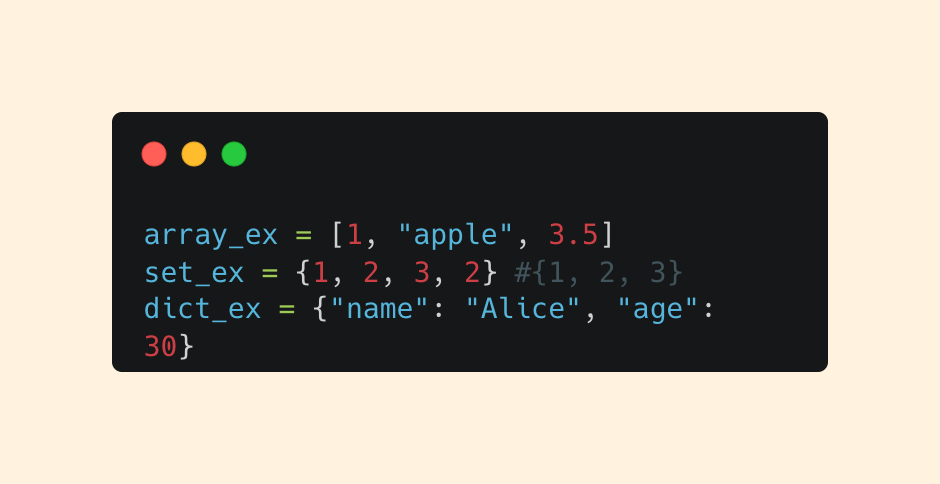
Collections
Array (list) - ordered, changeable (mutable) sequence
Set - unordered collection of unique values
Dictionary (dict) - key-value pairs
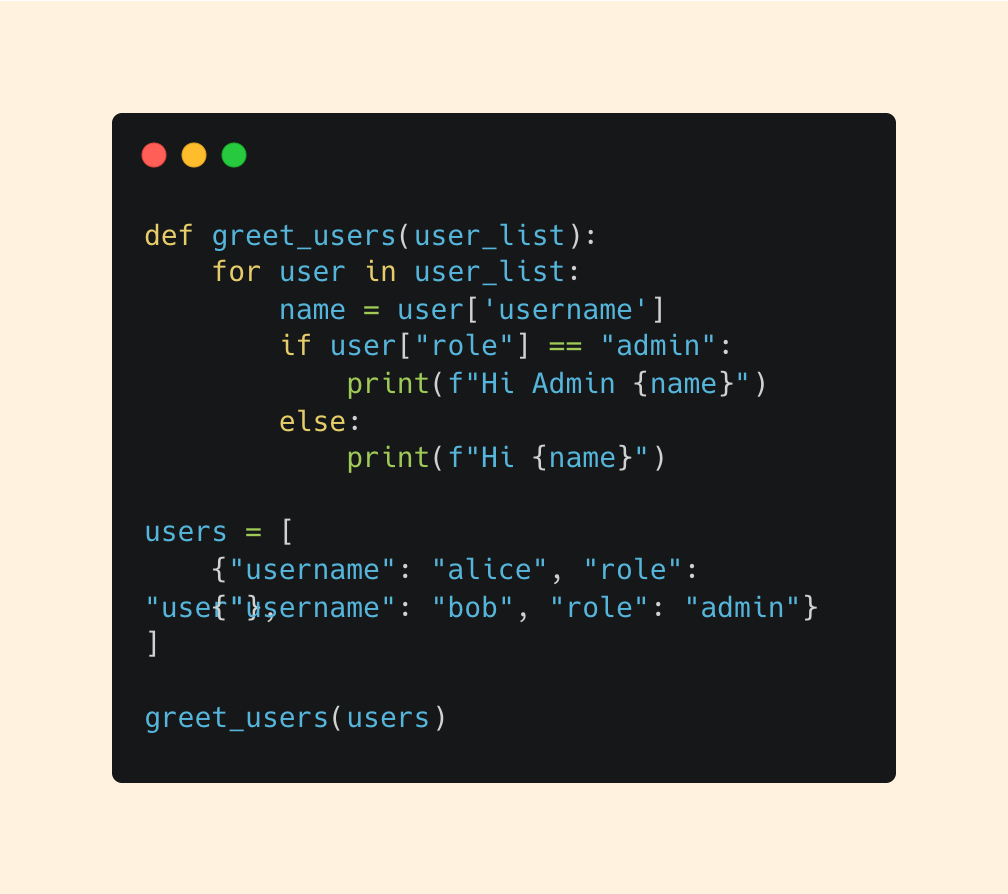
Basic Scripting
These control structures form the foundation of logic for any script.
if Statements - for decision making
for Loops - for iterate over data
Functions - for packaging and reusing logic
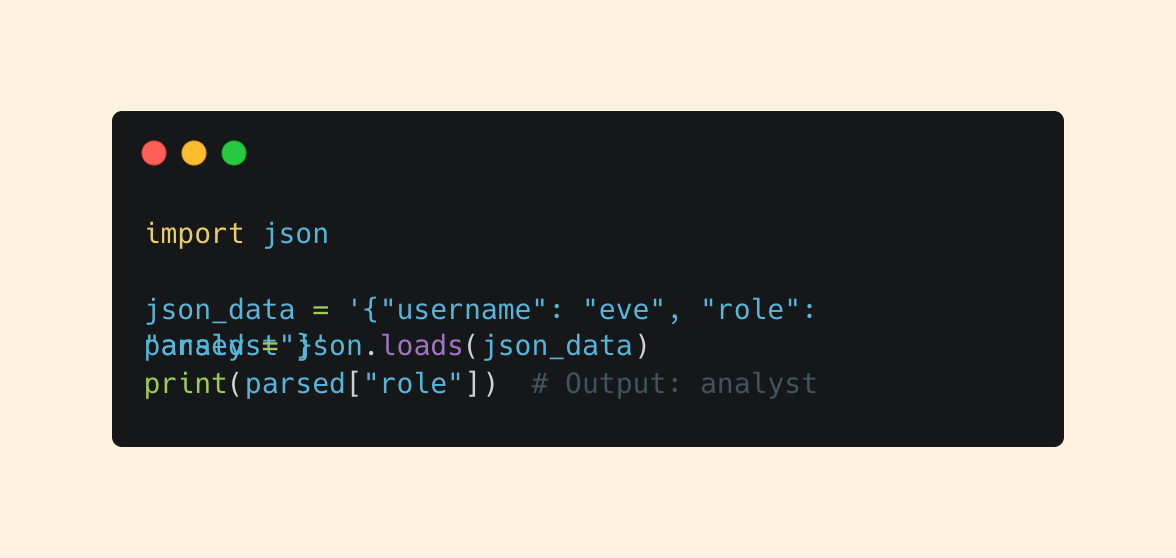
JSON
You’ll frequently encounter JSON data when working with APIs and logs. JSON (Javascript Object Notation) looks almost exactly like a Python dict, and Python has built-in tools to work with it seamlessly.
Advanced Concepts
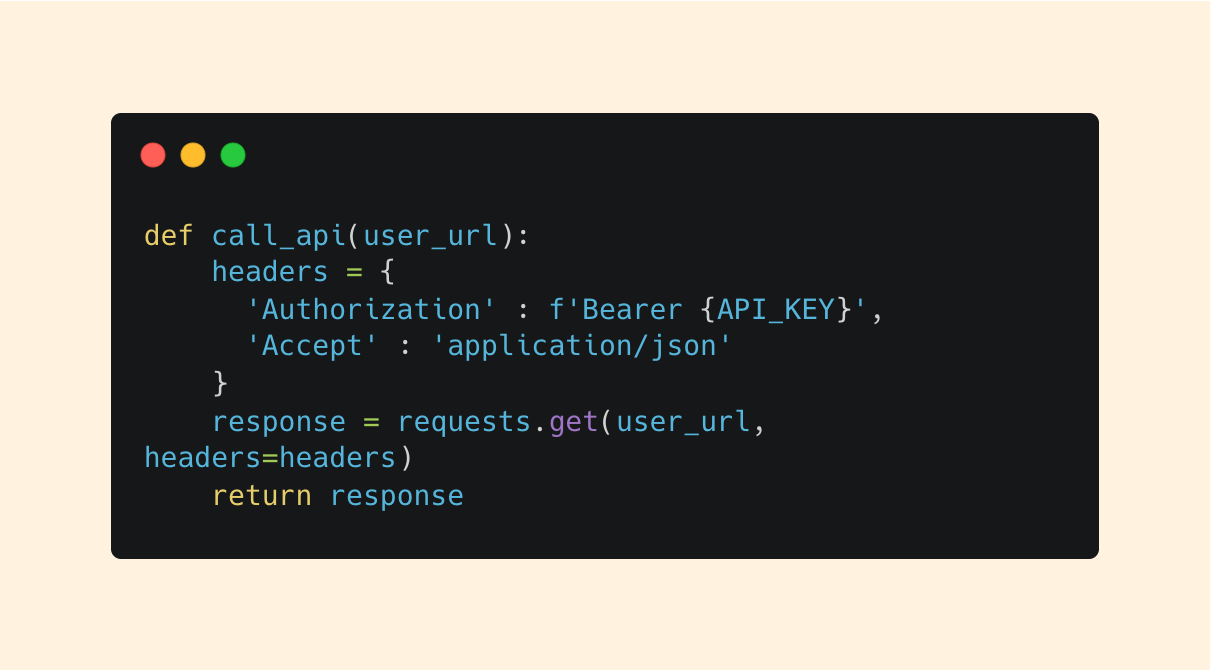
Security professionals frequently write scripts that talk to other tools via APIs.
Python has a library called requests that makes this simple:
requests.get()
requests.post()
requests.put()
requests.delete()
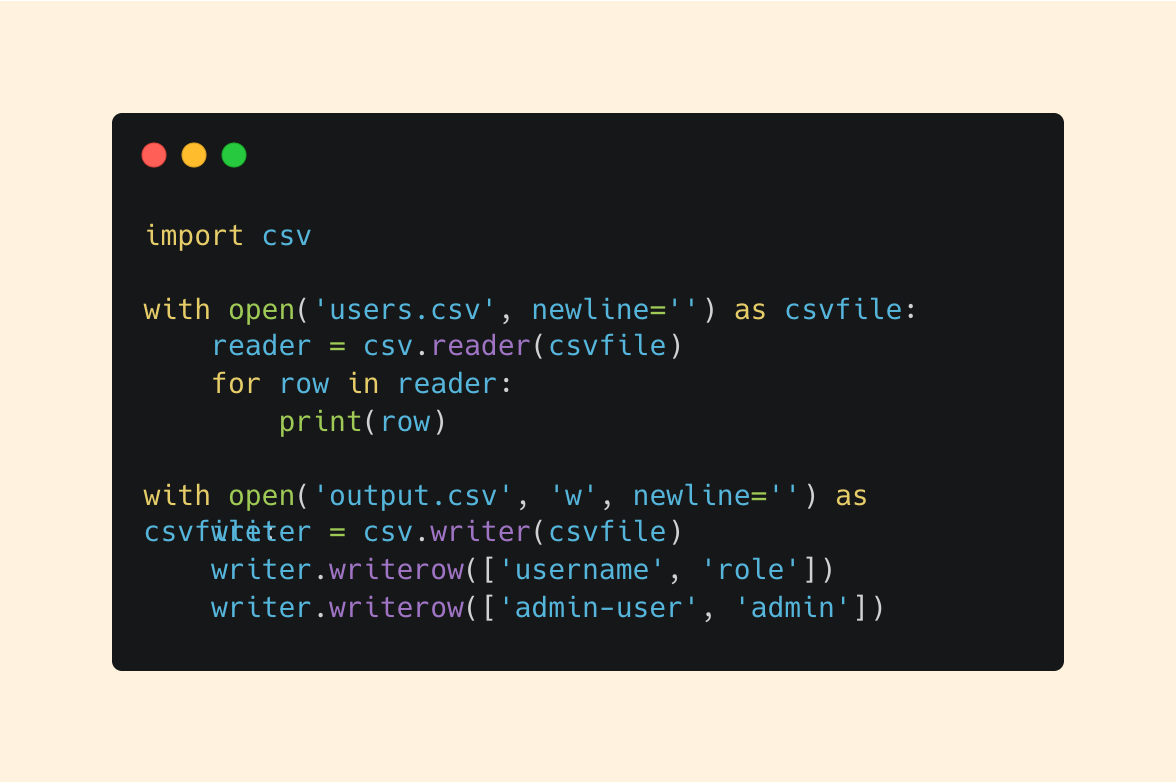
It’s common to work with CSV files. Whether you’re parsing logs or generating reports, Python’s csv module has csv.reader and csv.writer methods to perform these operations with ease.
Next Step
The best way to learn is by building. Try this project to apply everything above:
Build a simple Flask API in Python. Ask ChatGPT to help you brainstorm what it should do (but don’t let it code the whole thing for you). For example: upload a CSV of your weekly expenses and return them sorted by price range.
Then…
Create a CLI tool to talk to your Flask API. An example use case could:
Take a CSV filename from your local system
Send the data to your Flask endpoint
Write the returned response to a JSON file.
You have the tools. You have the blueprint - what are you waiting for?
The Cybersec Café Discord is officially live! Join a growing community of cybersecurity professionals who are serious about leveling up. Connect, collaborate, and grow your skills with others on the same journey. From live events to real-world security discussions — this is where the next generation of defenders connects. Join for free below.
Bonus Exercise: Web App Security
In today’s world of SaaS platforms and microservices, web applications are everywhere - so understanding how they work (and, just as important, how they break) is key.
One of the best beginner-friendly ways to learn is by using Juice Shop - a deliberately vulnerable web app that teaches security through hands-on hacking. You’ll explore these real-world concepts in a legal environment and gain insight into how websites actually work.
You’ll also develop essential debugging skills - like using browser developer tools to inspect requests and responses.
Pro Tip: Pair Juice Shop with Burp Suite - a powerful tool used by AppSec pros to intercept and manipulate HTTP requests. Their free Web Academy is one of my favorite online resources (unsponsored) and is a fantastic way to go even deeper and build confidence in your skills.
Why Being Technical Matters
Cybersecurity is more competitive than ever, and standing out is getting even harder. The industry is shifting, and technical skills are becoming a must.
The truth is, most people don’t put in the extra time to sharpen their skills. That’s your opportunity. It could be the difference between landing the job or missing it, getting promoted or staying stuck.
As professionals, we owe it to ourselves to keep growing. If you’ve been in the field and know your technical skills need work - this is your sign to start.
If you’re just getting started - this is your chance to build a strong foundation early.
If you already have the skills - double down and keep rounding yourself out.
Because at the end of the day, growth matters. And leveling up your technical skills is one of the most powerful ways to grow.
Securely Yours,
Ryan G. Cox
P.S. The Cybersec Cafe follows a weekly cadence.
Each week, I deliver a Deep Dive on a cybersecurity topic designed to sharpen your perspective, strengthen your technical edge, and support your growth as a professional - straight to your inbox.
. . .
For more insights and updates between issues, you can always find me on Twitter/X or my Website. Let’s keep learning, sharing, and leveling up together.






This was really a simple and nice article on cyber security which covers almost all concepts of it… great one
Thank you very much for sharing this!