Python for Security Engineers
Cybersec Café #40 - 11/5/24
I’ve talked to quite a few people over the last few years that are interested in pursuing a career in Cybersecurity.
But they’re scared to make the jump.
Why?
Because they don’t know how to code.
I’m here today to show you that you don’t need to be a software engineer building micro-saas products during your weekends to make the jump to cybersecurity.
Nope - here’s the playbook for the bare minimum skills to focus on to make yourself an asset in cybersecurity.
Why Python?
There are a plethora of languages out there to choose from these days that you’ll here different people recommending depending on their use case.
Don’t get me wrong, Javascript, Ruby, Go - all have particular things they’re good at.
But the one language that is practically everywhere is Python. Not to mention, a large majority of tools out there, whether emerging or established, support Python out of the box or add support later due to it’s popularity.
It also has some great benefits for people trying to break into the field:
The Syntax is relatively straight-forward
It’s a jack-of-most-trades language, but master of none
In order to get started, I’d recommend covering the basics:
If statements
Loops
Methods
Error handling (commonly overlooked)
Once you have these down, you’ll be ready to jump into specific use cases.
- Today’s Sponsor -
Prepare for a career in Cybersecurity, one sip at a time with The Security Sip. With rapidly evolving threats and technologies, many struggle to gain the right skills and experience to break into the cybersecurity industry. This course is designed to transform beginners into industry-ready professionals over 12 sections, 85 modules, and 155 exercises. Check it out!
APIs
In cybersecurity, programming is commonly used for interacting with various different applications.
We do this in the form of APIs.
The use case can vary depending on the project, but some common ones you’ll find are:
Performing OSINT
Connecting different software’s together
Creating custom scripts to automate processes
A lot of problems can be solved by buying a product nowadays. But if you want to be an asset to your team, you need to be willing to step in and try to build out a custom solution, especially if the use case is relatively simple.
To call APIs, its important to become familiar with how the Requests library works. It’s a simple library for Python’s to help facilitate your API requests.
Here’s an example of how simple it is to call an API:
This is a great sample of how an API request will function. Probably simpler than you would have thought, thanks to the requests library.
In this specific example, you’ll get a response variable that will give a response code, and response_json, which will give you your data to utilize from the request.
You’ll need to get used to reading API documentation, but once you’ve gotten a few under your belt, you’ll be able to crank these out in no time.
Processing Data
You’ll deal with quite a few different data types in security. Some common ones are:
JSON
XML
CSV
YAML
Most API services nowadays use JSON. However, you’ll undoubtedly run into instances in the wild where you’ll need to be able to process JSON or a CSV into your code in order to use it.
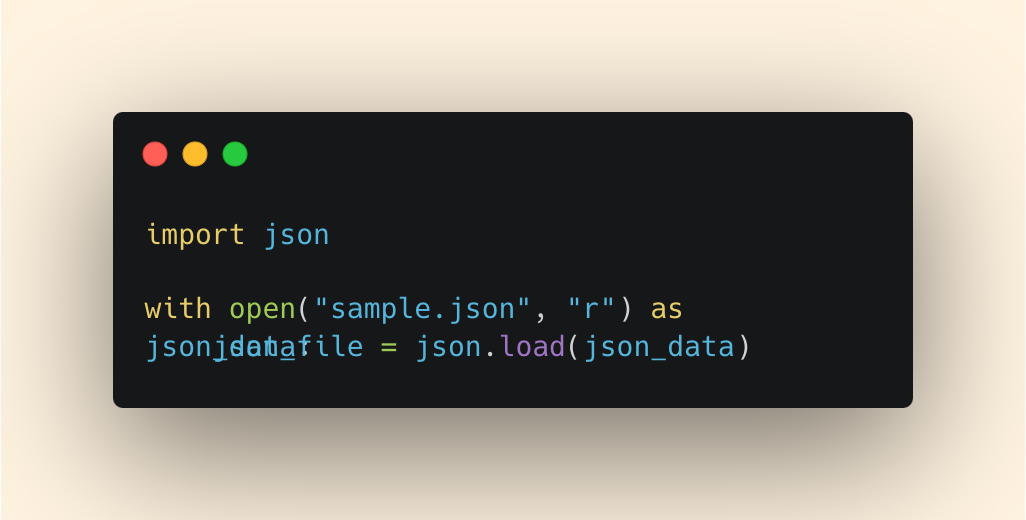
In order to process JSON in Python, you’ll need to understand the json library.
But don’t worry, it’s simpler than you think. Here’s how you can open a JSON file to work with the data programmatically:
Now, you have your data ready to go.
For XML and HTTP processing, you’ll want to get familiar with the Beautiful Soup library.
For CSV, there’s a library called csv (shocker, I know) that you’ll want to look into.
Working with Files
Just as you saw above, there are times where unfortunately, API endpoints are not available for you to interact with your data.
In these cases, you’ll have to understand how to read in data, just like we did above.
There are also cases where we’ll create data objects that we’ll need to write out to save. In this case, you can do the following:
Writing Detections
Detections can come in many different shapes and sizes.
You’ll find many tools that will deal with detections in YAML form, or in Query form.
But, if your goal is to have the chops to join a technically talented organization, you should understand basic logic in order to write Python detections.
An example would be something like:
In order to write these detections, you’ll need to work on your data analysis skills so you can understand SIEM logs.
But, you’ll also need the chops to write some basic Python logic.
If you want to dive deeper into writing detections, you can check out a blog post here.
CLIs and Apps
These two pieces are most definitely on the “nice-to-have” side of cybersecurity, and you’ll find it easier to figure out after getting comfortable with what I mentioned above.
CLI tools are an integral part of security, and you’ll likely be using quite a few that other people or companies have built.
But, you’ll certainly come across a time where you’ll have to build your own.
Now, there are many ways to build a CLI, and some can get quite complex using tools like decorators and classes. But, a simple tool would look something like:
Not too bad right?
The next piece would be for standing up your own APIs to use internally.
Luckily, Python has a great library for you to use that could get you an API stood up in minutes.
Check out Flask and create a simple Flask App for yourself to test locally.
It’s a great way to not only see how Web Applications function, but also can help you build a service for yourself.
Put it All Together
As you can see, learning Python for cybersecurity is not nearly as intense as you would think.
You can put some simple concepts together and have more than you would need to get started in the industry.
Want to get started today? Here’s what I’d suggest. Take a weekend to:
Standing up a Flask app to solve a use case for your own personal life
Make a CLI tool to interact with it easily
Create different file types to send to your new API endpoint to process
Having trouble figuring out what to solve? How about a service to help organize your finances!
Now you have the blueprint, what will you do with it?
Securely Yours,
The Cybersec Cafe
Just a heads up, The Cybersec Cafe's got a pretty cool weekly cadence.
Every week, expect to dive into the hacker’s mindset in our Methodology Walkthroughs or explore Deep Dive articles on various cybersecurity topics.
. . .
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X or my Website. Can't wait to keep sharing and learning together!