No, they’re not the flashiest part of Security Engineering. But if you want a scalable, world-class Security Operations function, they’re absolutely essential.
I’m talking about Playbooks - the step-by-step documentation your team relies on to triage alerts, mitigate threats, and respond to incidents consistently and effectively.
With the volume of alerts that modern SOCs handle, it’s inevitable that processes will get lost or forgotten - whether through turnover or just the chaos of daily operations.
Most teams store documentation somewhere like Confluence, GDrive, GitHub, or Notion. Inside you’ll find the play-by-play steps for identifying, triaging, responding to, and remediating various security events.
But Playbooks are not just limited to SIEM alerts.
You can have them for phishing, vulnerability management, incident response, threat hunting - even your daily workflows. If you're repeating a process more than once, it’s probably worth turning into a Playbook.
At the end of the day, the goal is simple: streamline operations, drive consistency, and keep your team efficient with as little guesswork as possible.
Let’s walk through how to build a great Playbook with a realistic scenario.
Subscribers get access to the Playbooks Repository in Cybersec OS to follow along with this article!
Scenario
You’ve just started ingesting GSuite logs into your SIEM. While some out-of-the-box detections offer basic coverage, you’re not confident it’s enough.
So, you create a custom detection: GDrive Excessive Sharing to External Non-Business Emails.
The idea? Catch early signs of potential insider threats by flagging unusual volumes of sharing to non-business emails.
The detection logic is ready to go live - but before it does, it needs a solid Playbook to guide your team in the case it does fire off.
Drafting Your Playbook
Start with Purpose
There’s no one-size-fits-all approach to writing Playbooks, but one habit I’ve found especially helpful is starting with a purpose statement.
This sets the tone. It tells the reader exactly why this Playbook exists, without diving into too many technical weeds. It should be a one-line (or two) that answers: What is this Playbook helping us do?
This not only gives context to the person executing the Playbook, but also helps future-proof the doc by anchoring it to a clear goal.
Purpose
This Playbook supports the “GDrive Excessive Sharing to External Non-Business Emails: detection. It’s designed to help identify potentially malicious insider behavior by investigating the user suspected of sharing large volumes of files to non-customer, public email providers within a 24-hour period. Use it to filter out legitimate business activity and focus on suspicious sharing patterns.
Give a Description
Next, add a brief description of the alert this Playbook is tied to. Think of this as the “what fired” explanation - not the why, just the what.
It’s less about the process and more about quickly giving your team a mental model of what the detection means and what triggered the response.
This should be short and simple, ideally no more than a sentence or two.
Description
A user has shared an unusually high number of files to external email addresses. It may indicate unauthorized data sharing or insider threat behavior.
Investigation
Now it’s time to walk the reader through exactly how to investigate this alert.
Your goal here isn’t to write an essay - it’s to build a checklist of actionable, repeatable steps that guide someone through the early stages of triage.
Use short, direct instructions and include quick links to essential tools like dashboards, IP lookups, saved queries, or relevant docs whenever possible.
Investigation
Investigate the filenames and the external email addresses flagged in the alert using GDrive External Share Dashboard.
Assess sensitivity of shared files. Check if file names suggest sensitive content, like financial, customer, design, sales, or architectural documents.
Identify potentially suspicious recipients. Look for personal or unrecognizable email addresses. Signs of a potential insider threat include: the user’s own personal email, a team member’s personal email, an unknown email, or a competitor.
Use the Investigate User Dashboard and Investigate IP Dashboard to view recent behavior and access patterns tied to the user and associated IPs.
Leverage IP Reputation Tools to validate legitimacy. (VirusTotal | Talos Intelligence)
Use Recent Activity or Common Activity from the GSuite Saved Query Knowledge Document, or use the GDrive External Share Query shown below for a more tailored look.
Leverage Selecty to build or refine queries quickly. Iterate as needed to dig deeper into file access, sharing patterns, or privilege escalation.
Start forming hypotheses based on the user’s activity and context. Begin forming a narrative.
Was this accidental? Intentional? A pattern? You don’t need to prove it yet, but mentally sketch an outline.
- Today’s Sponsor -
Selecty is a database-agnostic, sidecar query assistant - built to integrate seamlessly into your workflow without dulling your edge. Generate smart, contextual queries, optimize them to your use case, break them down into plain English, and debug faster than ever - all in one sleek interface. Check it out!
Triage
Once your initial investigation is complete, it’s time to triage the alert - decide what action, if any, should be taken.
The goal here is to help analysts move from “What’s happening?” to “What should we do about it?” based on common outcomes. Provide clear guidance based on potential investigative findings.
Triage
If files don’t appear sensitive & no malicious activity is detected:
Follow up with the user. Ask why they’re sharing files externally.
Educate over enforce. Many users share files with themselves for convenience or to move data between personal and work devices.
Remind them of the risks and reinforce that intermingling work and personal data is against policy - even if intentions are harmless.
If the user says they’re using personal software to improve their workflow, remind them that only approved tools are allowed for security reasons. Encourage them to submit a request if they believe a tool should be reviewed.
If files appear sensitive or potentially malicious:
Escalate to the Security and IT teams. This includes documents like customer lists, IP, legal agreements, etc.
Context matters. Some users may share personal accounts for malicious reasons, but others may be confused or misinformed.
Gauge the user’s intent and context before jumping to conclusions.
Assess for Insider Threat indicators. Reach out to the manager in a shared DM (with Security team) to keep communication private but visible. Look for red flags:
Are they leaving the company?
Are they launching a competing business?
Have they expressed dissatisfaction or disengagement?
If malicious intent is suspected:
Don’t tip them off. Continue monitoring their activity quietly to collect more evidence.
Coordinate internally and prepare contingency plans.
If risky behavior continues, escalate further. Get security leadership approval and work with IT to disable access and secure data.
Queries and Links
This section is meant to make both Investigation and Triage as seamless as possible.
While hyperlinks should be embedded throughout your Playbook, this is your central hub that brings everything together. It’s okay (and encouraged) to repeat hyperlinks that appear earlier in the document. That way, readers know they can simply scroll here when they’re in a hurry.
Include direct links to dashboards, saved queries, detections, and related documentation that your team relies on.
Queries and Links
Use the GSuite Saved Queries document to find your general saved queries to investigate the log source.
Dashboards:
Investigate User Dashboard: Get a holistic view of the user’s recent activity across services.
GDrive External Share Dashboard: Focused view of all files shared externally from Google Drive.
IP Investigation Dashboard: Helps identify suspicious or rare IP activity associated with the user.
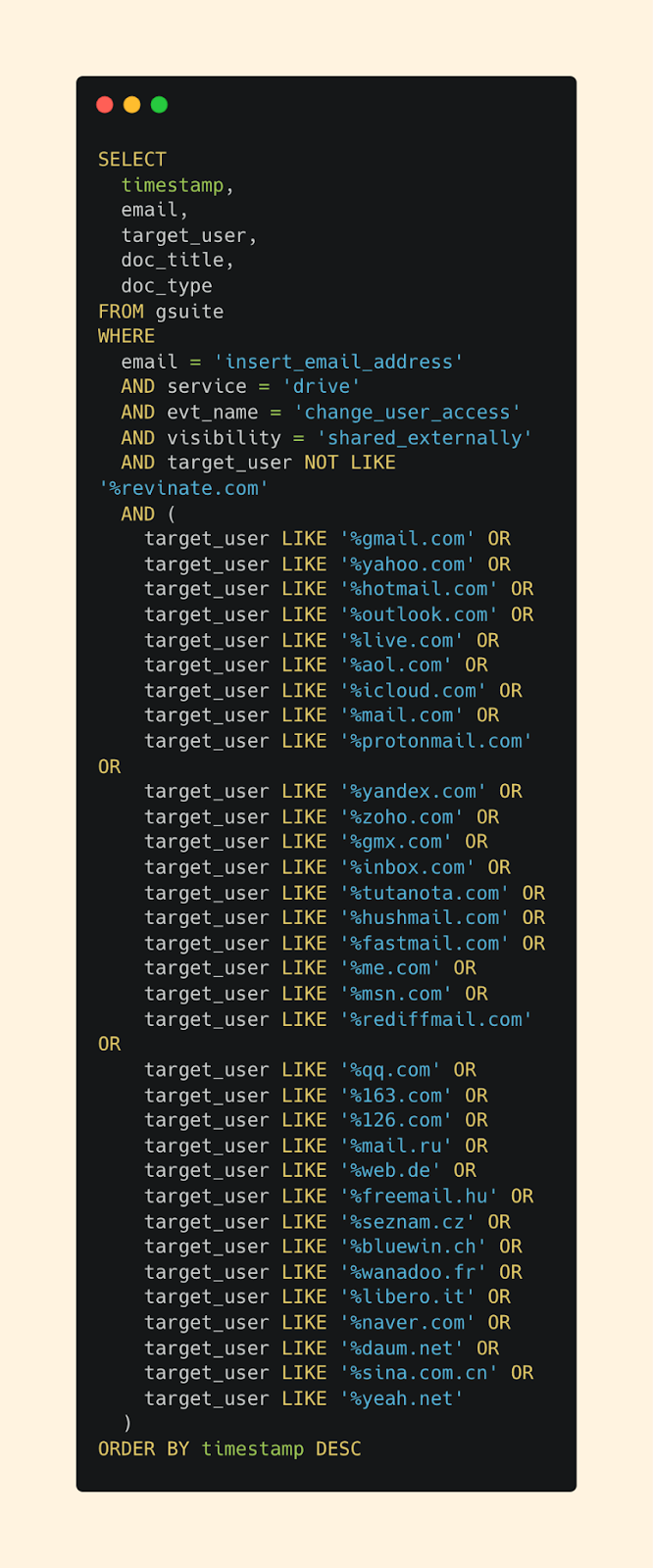
GDrive External Share Query
Use this query to identify which files the user shared externally, including the target email addresses. Replace insert_email_address with the address of the user under investigation.
Escalation and Response
This section outlines the recommended actions based on possible outcomes from your Investigation and Triage steps.
Each case below is framed to guide the analyst in deciding whether to close out the alert, take educational action, or escalate further
Escalation & Response
False Positive
Indicators
No sensitive files shared.
Target email appears benign.
Actions
Reach out to the user with a reminder about the risks of transferring files between personal and work devices.
Use an educational tone - highlight security concerns rather than applying blame.
Confirmed Activity
Indicators
File shared with a customer who lacks a custom domain.
File content is not sensitive, or applies to the customer.
Actions
Confirm the customer relationship with the user and/or team.
Document the outcome and details in the ticketing system for future reference.
True Positive (Benign)
Indicators
Files shared with the user’s personal email.
Files are not sensitive, but this violates policy.
Actions
Educate the user about company policy and risks.
If a pattern emerges or the user is noncompliant, escalate to their manager for reinforcement.
True Positive (Malicious)
Indicators
Files contain sensitive company data.
Shared with a personal or suspicious external email.
Action
Escalate to the Security team immediately.
Consider insider threat potential; do not alert the user.
Involve the manager discreetly if additional context is needed.
Coordinate with IT for user access restrictions if malicious intent is confirmed.
Version Control and Tags
Maintaining version history and tagging is essential for Playbook lifecycle management. Whether you’re using GitHub, Confluence, or another platform, make sure every update is recorded and traceable.
Version and Tags
v1.0
Created: 6/17/25
Updated: 6/17/25
Tags: GSuite, T1537, T1020, T1087.004, T1071.001
💬 Tell me about a time when you were really glad your team had a playbook in place. What happened, and how did it help you in that moment?
How Playbooks Help Your Security Team
There’s no way around it - Playbooks are essential to any high-functioning security team, and building them is a collective responsibility.
They don’t just document what to do - they preserve critical knowledge. Whether a team member leaves, a process is rarely used, or you’re deep in a fast-moving investigation, Playbooks ensure that nothing gets lost and no one is left guessing.
Playbooks can help you turn chaos into action.
They allow your team to:
Respond to threats quickly and confidently without reinventing the wheel.
Empower junior analysts, new hires, and even non-security collaborators to contribute meaningfully.
Maintain consistency and quality as your team grows and scales.
Build automation on solid, vetted foundations - turning tribal knowledge into executable workflows.
They’re more than just internal documentation, Playbooks are operational guardrails. They reduce risk, improve efficiency, and help your team operate without fear of making the wrong move.
So next time you find yourself doing something more than once - take the time to write the Playbook. Your future self (and your team) will thank you.
Securely Yours,
Ryan G. Cox
Just a heads up, The Cybersec Cafe's got a pretty cool weekly cadence.
Every week, expect to dive into the hacker’s mindset in our Methodology Walkthroughs or explore Deep Dive articles on various cybersecurity topics.
. . .
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X or my Website. Can't wait to keep sharing and learning together!